Cybersecurity threats today don’t just knock; they kick the door wide open.
In recent years, healthcare has faced some of the most disruptive and large-scale cyberattacks in history. While the headlines often spotlight massive health systems or insurance giants, private practices haven’t been spared. Indeed, small clinics and solo providers are increasingly attractive to attackers: the data is just as valuable, but defenses are typically weaker.
For smaller practices, the stakes couldn’t be higher. A single breach can shut down operations, compromise patient trust, and even threaten your practice's future. What’s more, the idea of a “cyberattack-free normal” no longer exists.
Cybercrimes are now part of the healthcare landscape, and bulletproofing every system isn’t realistic. The real strategy lies in anticipating risks, building resilience, and minimizing the blast radius when, not if, an incident occurs.
Against that backdrop, it’s crucial to understand the specific factors driving these threats and the steps private practices can take to strengthen their defenses.
Cybersecurity threats in healthcare aren’t distant possibilities; they’re live explosives waiting to go off. Every click, every unsecured device, every outdated vendor connection has the potential to ignite a chain reaction that compromises patient safety and trust.
In 2024 alone, more than 276 million patient records were exposed or stolen, an average of 758,000 records per day. That’s nearly the entire U.S. population as potential victims of identity theft or medical fraud within a single year.
For years, 2015 was regarded as healthcare’s darkest moment, when Anthem, Premera Blue Cross, and Excellus collectively lost 112 million records. But the 2024 Change Healthcare attack rewrote the history books, exposing 192.7 million records in a single blow. It was a brutal wake-up call: a single breach, from a single vendor, can disrupt the entire healthcare ecosystem.
And the bombs keep ticking. In 2025, the breach at Yale-New Haven Health and Episource, LLC compromised more than 10 million records, reminding us that even major systems with advanced IT teams aren’t immune.
This underscores a significant question: if billion-dollar health systems with full-time cybersecurity teams are struggling, what does that mean for smaller private practices?
Health data is one of the most valuable assets on the dark web, and cybercriminals are well aware of it. The financial stakes are astronomically high. In 2024, the average ransomware payment in healthcare reached $4.4 million, a cost that could cripple or even shut down a small practice.
For private clinics, the risk is even more severe. You handle the same sensitive patient data as large health systems but often lack their security infrastructure, staff, and budget. This makes you an attractive target, not because of a single flaw, but because of a web of vulnerabilities that attackers can exploit with alarming ease.
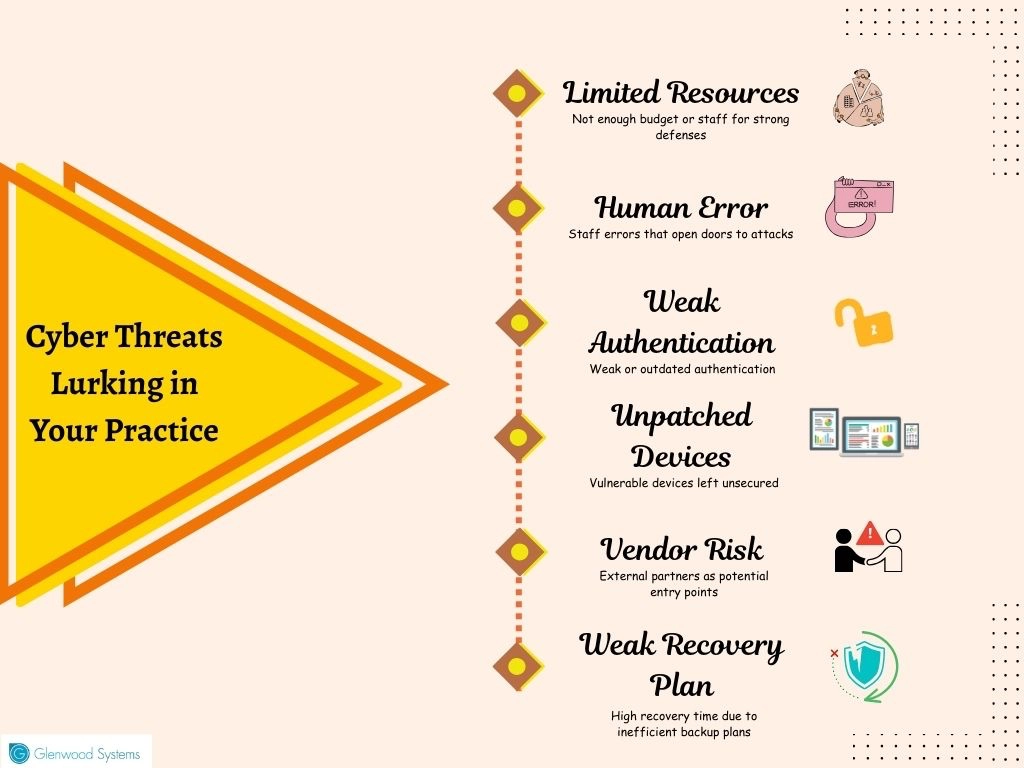
Here's what's putting private practices at such risk:
Hackers are evolving, exploiting every gap they find. It’s time to close those cracks and reinforce your defenses.
Cyberattacks don’t stop at screens; they can silence EHRs, disrupt monitoring, and stall treatment. With healthcare among the most targeted industries and attackers constantly evolving their tactics, the question is no longer whether you’ll be targeted, but when.
Now it’s time to turn the lens inward; identify vulnerabilities and reinforce cybersecurity. Here’s how:
Even the most prepared practices have blind spots. Vulnerabilities don’t all look alike; some lurk in outdated systems, others slip in through vendor connections, weak authentication, or forgotten accounts. Conducting a risk assessment and mapping these vulnerabilities is the first step toward building a resilient defense.
Legacy Systems
Old operating systems, unsupported EHR modules, and outdated imaging archives often slip through without regular patching, making them easy targets. Maintain an up-to-date inventory of technology used to handle patient data, and replace or patch unsupported devices. In addition, accurately budget for upgrades to prevent delays.
Vendor & Third-Party Risks
Every billing partner, telehealth platform, and cloud storage provider expands your attack surface. If a vendor fails to follow strict compliance standards, their weakness becomes your liability. Require proof of compliance with HIPAA and NIST standards, and regularly review vendor access privileges. Any connections that are no longer necessary should be terminated promptly to avoid exposure.
Shadow IT
Unused logins or “shadow” software not sanctioned by IT create dangerous blind spots. Because they’re often unpatched or unsecured, they become prime targets for attackers. Keep a real-time inventory of all accounts, devices, and applications. Audit credentials monthly and retire unused ones to close off hidden entry points.
Weak Authentication
Password reuse and single-factor authentication leave portals, billing systems, and VPNs vulnerable to cyberattacks. To strengthen access, move beyond passwords and require authenticator apps or hardware tokens for EHRs, patient portals, billing systems, and cloud platforms. These measures thwart credential stuffing attacks and ensure compliance with HIPAA technical safeguards.
The healthcare attack surface is vast, spanning EHRs, imaging systems, connected devices, and third-party vendors. Trying to lock down everything at once isn’t strategic or sustainable. Instead, effective security begins with smart prioritization guided by risk assessments: focusing first on risks that pose the greatest threat to patient safety or data security and can be remedied with relatively low effort and cost. High-impact, low-cost safeguards should come first.
Start with your crown jewels: systems that directly support patient care and store sensitive information, such as your EHR, imaging labs, medications, and ORs. These are the assets attackers most often target, and the ones where downtime or breaches can have the greatest impact.
Make risk management part of your financial planning. Tie every assessment to your annual budget so remediation funds are not theoretical. This way, you can act on risks as they’re identified, rather than scrambling for resources after an incident.
The Cisco Cyber Threat Trends Report found that 74% of CISOs rank human error as their top cybersecurity risk. The message is clear: without continuous cybersecurity training, even the strongest defenses can collapse. Simple slip-ups, such as falling for phishing emails, reusing passwords, or misdirecting data, often become the doorway attackers need.
Once-a-year training fades fast; building resilience requires regular, reinforced learning. Implement:
Phishing remains the leading entry point for cyberattacks in U.S. healthcare, which makes email security a frontline defense. To reduce risk, healthcare organizations should combine technical safeguards with staff awareness:
Measuring progress against a trusted framework helps healthcare organizations avoid blind spots. The NIST Cybersecurity Framework (CSF) remains the industry gold standard, which offers a structured way to evaluate strengths and gaps across five key areas: Identify, Protect, Detect, Respond, and Recover.
Rather than relying solely on rules and tools, employ penetration testers and red teams to simulate real-world attacks and expose weaknesses before hackers do. The cyber threat landscape is shifting rapidly, so agility means continuously monitoring emerging threats, updating defenses, and revising response plans.
Even the strongest defenses aren't bulletproof. The true measure of preparedness is how swiftly they detect, respond, and recover. Monitor critical metrics, such as mean time to detect (MTTD), mean time to respond (MTTR), and mean time to recover (MTTRc), to track and improve readiness.
Follow the 3-2-1 backup strategy: maintain three copies of important data on two different storage types, with one copy offline. Conduct quarterly full-restore tests, including EHR databases and imaging archives, to verify recovery speed.
Additionally, practice transition to analog procedures during downtime, from paper charting to manual scheduling, so patient care continues even if digital systems are offline.
Lastly, have a printed incident response plan that lists responsibilities for contacting insurers, regulators, and vendors, ensuring action is taken even if systems are encrypted. Practices that build resilience can weather attacks while maintaining care delivery with minimal disruption.
Healthcare runs on trust, and nothing erodes that faster than a cyber breach. Attackers aren’t waiting, so neither can you. The path forward isn’t about checking boxes; it’s about a collaborative effort to bolster defences.
At Glenwood Systems, we uphold data security as a core responsibility. Our platforms are fully HIPAA-compliant, and our servers are protected by advanced SSL encryption to ensure sensitive patient data remains secure. We believe every click, every record, every connection deserves the highest level of protection.
Reinforce Security. Protect Patients. Strengthen Trust.
Schedule a Free Consultation!
